Having spammers sending emails that pretend to come from your email address is worrying and can seriously damage your reputation or lead to financial fraud eg by giving people fake logins or announcing change of bank details. But how do you try and stop it?
Read more: How to Stop Email Spoofing using DMARCDMARC, SPF and DKIM
Various attempts have been made to eliminate this problem and a good solution now exists, at least for email clients like GMail and Outlook. Other email solutions like Thunderbird may not work as well.
The basic system is to create an email reporting policy called DMARC on your web server. This tells email programs what checks to do with your emails and how to respond to failures. Just having a DMARC policy improves email deliverability.
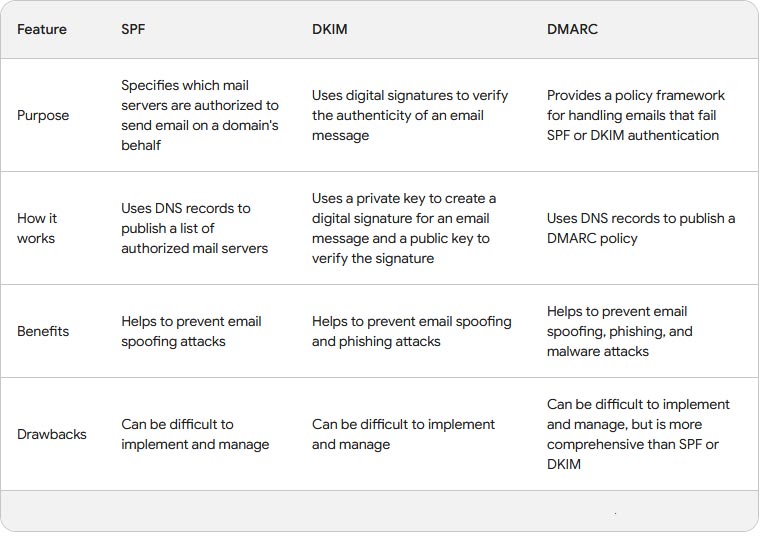
DMARC includes two different checking mechanisms, Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM), which we will discuss after setting up DMARC policy.
Setting up your DMARC policy
This needs to be setup on the web site control panel for your email domain e.g. for Example.com emails this must be on Example.com server as this is where GMail etc. will look for it as part of the site’s DNS records. It doesn’t matter if you use a different email service, checks must be on your web server.
Change example.com in examples to your own website.
Go to your Control Panel and find DNS Editor – in CPanel this is called Zone Editor. You need to add a new TXT record.
| _dmarc.example.com. | 14400 | TXT |
Record Value: v=DMARC1;p=none;sp=none;adkim=r;aspf=r;pct=100;fo=1;rf=afrf;ri=3600;rua=mailto:support@example.com;ruf=mailto:support@example.com
Important Points
- Name must be _dmarc.example.com – change to your site
- v field must be DMARC1
- p field is the policy for failing emails. Set this to none until testing is complete and update later to quarantine or reject
- rua and ruf fields are email addresses that receive reports from Google, Outlook etc so you can see results.
- Other fields can be left as default
You now have a DMARC policy that email clients can check. As p=none, your emails will not be affected until you change p to be quarantine or reject. We now need to setup the actual checks that will be performed, SPF and DKIM.
Setting up SPF
SPF or Sender Policy Framework identifies the server(s) which is allowed to send emails. This might be your server name, a fixed IP address or a third party email site.
Set up another TXT record with these parameters
| kanda.com. | 14400 | TXT |
What the record is depends on your email setup but here are some examples
- The record must start with v=spf1
- Own server example: v=spf1 a:example.com ~all
- Own server using MX record if they are set: v=spf1 mx ~all
- Own server using fixed IP address: v=spf1 ip4:192.168.0.1 ~all
- Own server using IP address range: v=spf1 ip4:192.168.0.1/16 ~all
- Using a third party mail server : v=spf1 include:_spf.mailsender.com ~all
- ~all should end record
These instructions define which server or servers are allowed to send emails with the From header set to example.com. They can be combined so your own server and an included 3rd party server can send emails.
Now when you send emails, the receiving email client will check on example.com for the SPF record. It will check if the email server that sent the email is listed in SPF record. If it isn’t, it will fail SPF.
What it does then, depends on your DMARC policy defined above. If p is set to none, it just records it, otherwise it quarantines it or rejects it
Setting DKIM record
DKIM is DomainKeys Identified Mail, which uses a public:private key pair to check email sender is valid. This needs setting up in your email sender as well as in your DNS records. DMARC will pass if either SPF or DKIM passes so this mechanism is not strictly necessary but is good practice.
Record in Email header
It is best to set this up in Email server first and copy key and selector to DNS record once you have them. Ask you third party email supplier or set it up in your own email server. In CPanel this is in Email -> Email Deliverability. This can also install DKIM and SPF records if you prefer.
Here is an example DKIM Signature that will appear in email header. This must be setup either on your own email server or by your third party email server.
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed; d=example.com; h=message-id :date:mime-version:to:from:subject:content-type :content-transfer-encoding; s=20230609; bh=UmoYgns4KYnPhcLLnK9MV TH0Ds0CSIwHJU1lzfa0c1A=; b=F2Vb+wJrzGLk00oubROX2DuKAgr6TZiCQ5own NJqy6Bf1olZcwydzDzJsh6s6UAkgX5X4gwCgHAfdNQJvtkXPqvDmVwzrgDJsoiMsuIbis0207gMl+gDzPC37eLlevRsuN3DihPXyN5OhwwF4Gjw8B8Khg+qF7Om4mFEHTZSFhFulJmxlk80hJvFIvZGJOvPey71OtNWsUUhpQhxJjO537DMTWe7BUWdqGlZUVYpzjF5lDlU4GJjNCMghz2KNGOAQxPxRZuUpiZsLgwUiqUiKCAntBr/6HXpt V3rE n0OIhTXgRIYoZ1/05WOuKJoONY3MHevVgimgbj2TEpKjHgw==
- d=example.com is real sender
- s=20230609 is the selector which must also appear in DNS record
DKIM DNS Record
You can get selector and key from your email server once you have set it up. CPanel can set this up automatically once you define DKIM in email server.
Set up another TXT record on your server
| 20230609._domainkey.example.com. | 14400 | TXT |
This is a domainkey and the number at the beginning, here 20230609, is called the selector and must match selector put in email header by email sender.
The record itself is the key, which much match the key in email header. Here is an example
v=DKIM1; k=rsa; p=ASND56VCHHgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAnus JpE+BwMl78spb6LqLhuB2cK5P4HHlqTb/79hviNN6Vm68EQO6hpZro /1o4yKn2ejPmfriU9trMraYNkS+Zv9FTsPwnruUUTeZqE3O7C9RySy7kT GK+Uklduehf+TWslGzcpeNCzJgAn0Uc51VS9Y985HHdUgJNXBF9LmfGeVZRrEVkcgXvhGGdkBp
- The record must start with v=DKIM1
- k defines encryption type, in this case rsa
- p is the actual key.
Testing and Checking.
Now you have set it up, you can test if it is working. Your emails won’t be affected. The first check is to use a tester and best one is on Dmarcian.com
DMarc Domain CheckerThis site has examples and will do it for you for a fee. Here is a full SPF syntax guide for example.
SPF Syntax GuideReport Emails
If you added an email to your DMARC policy as described before, you will receive zipped XML files from Google and Outlook. These show emails, including spoof attempts, that have been received that have From header set to your email address.
You can see if your genuine emails are passing SPF and DKIM and hopefully that spoof attempts are failing.
Checking in GMail
If you have a Gmail account, send an email to it from the email you want to check. In Gmail, click on More symbol in email (3 vertical dots) and select Show Original.
As well as the full header information, which includes SPF, DMARC and DKIM, it gives a Pass/Fail summary at the top. It might take a couple of days to update though.
| SPF: | PASS with IP 62.128.183.135 Learn more |
|---|---|
| DKIM: | ‘PASS’ with domain example.com Learn more |
| DMARC: | ‘PASS’ Learn more |
Summary
Conclusion
Once everything passes on Dmarcian.com and in Gmail, you can update your DNS DMARC1 record so that p=reject. At this point, emails that fail because they are a spoof attempt will be rejected by email client.
